Configuring OAuth via Keycloak
KISTERS WISKI deploys Keycloak as Identity Provider. In order to configure Keycloak for TISGraph, follow this guide:
Create Client in Keycloak
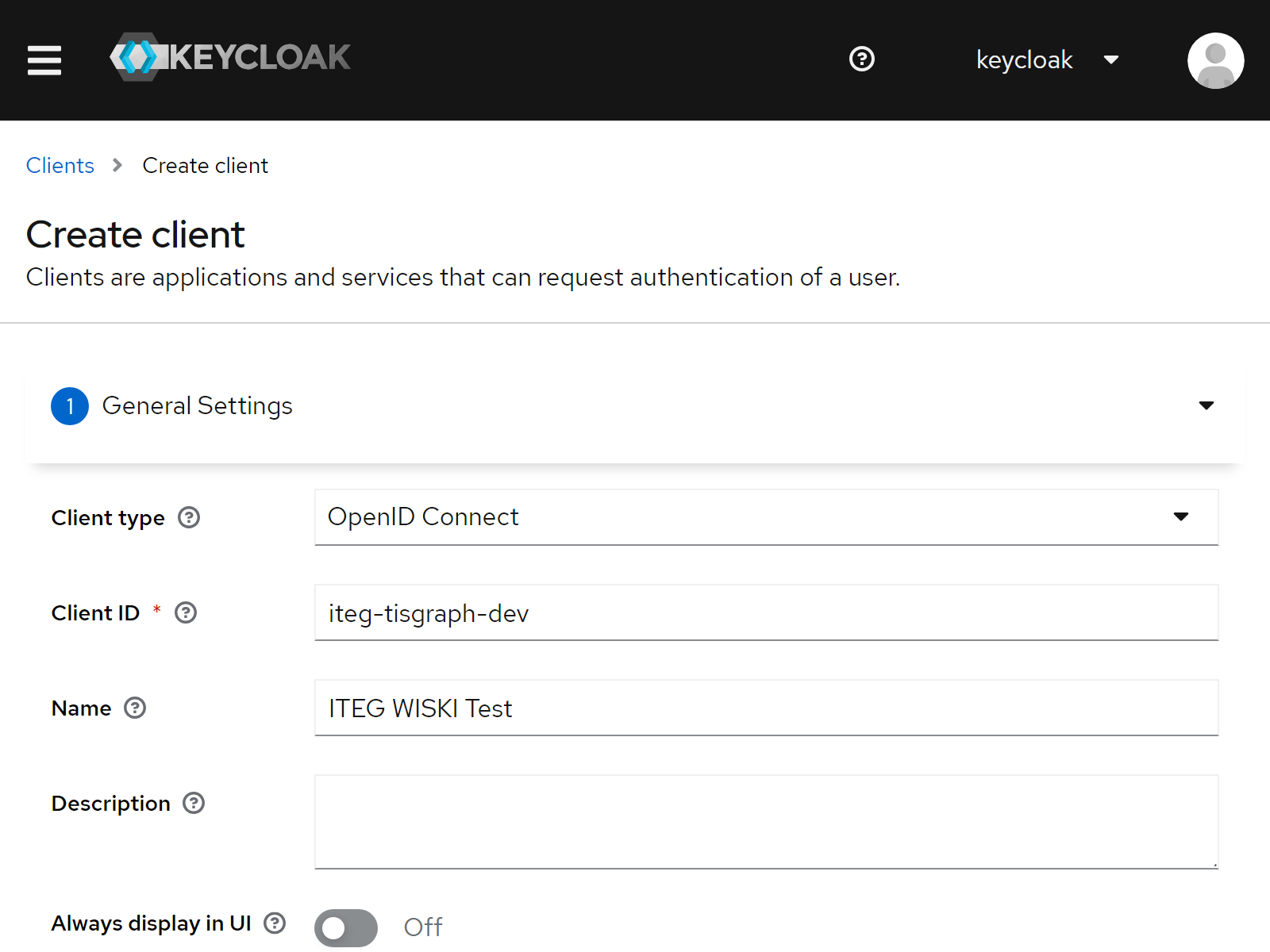
Firstly, navigate to https://wiski.example.com:7415/admin/master/console/#/kisters-water-default/clients and click "Create client".
In the wizard, configure the following
| Step | Name | Value |
|---|---|---|
| 1 | Client type | OpenID Connect |
| 2 | Client ID | iteg-tisgraph-dev |
| 3 | Name | ITEG WISKI Test |
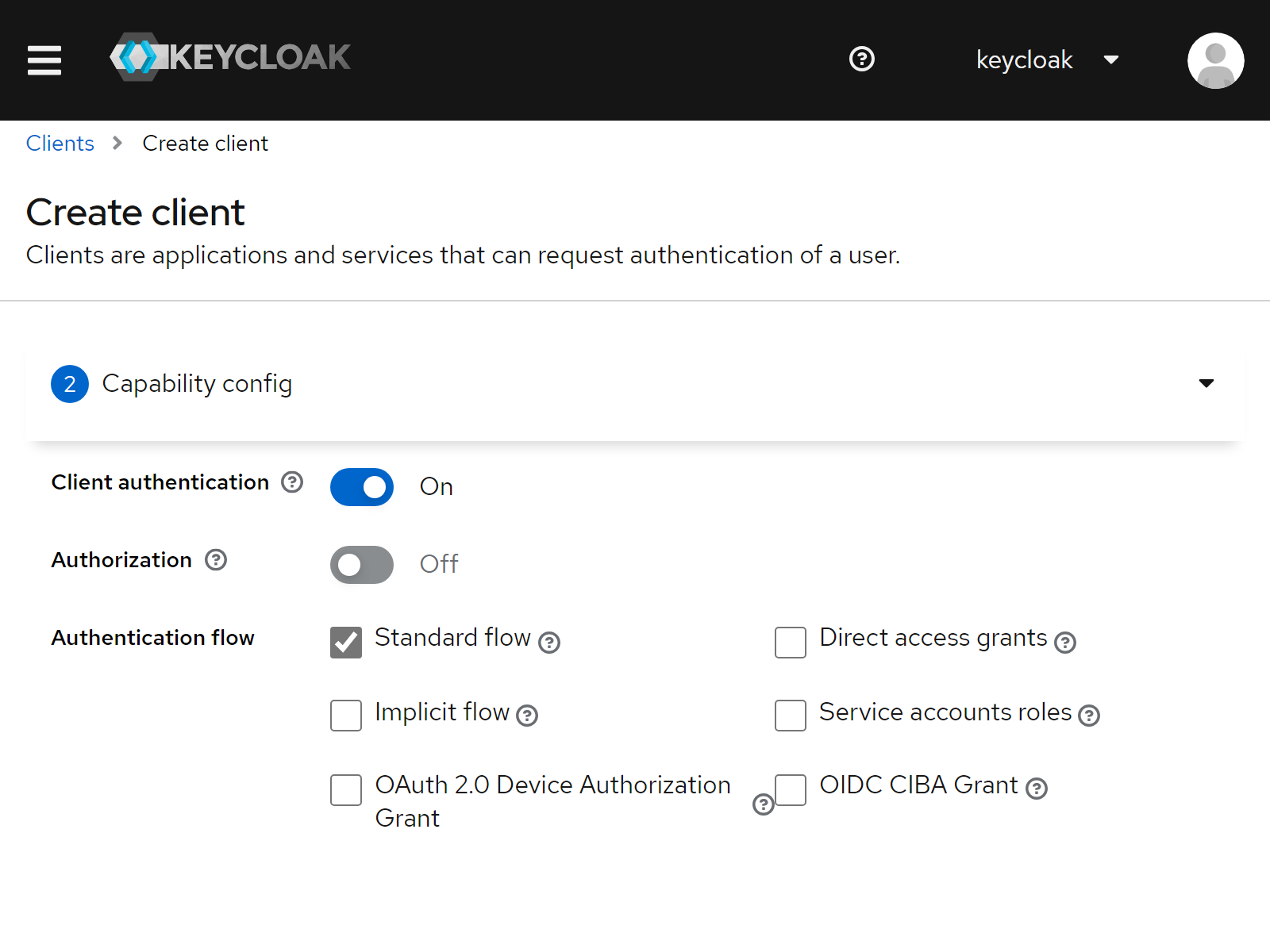
| 4 | Client authentication | On |
| 5 | Standard flow | On |
| 6 | Direct access grants | Off |
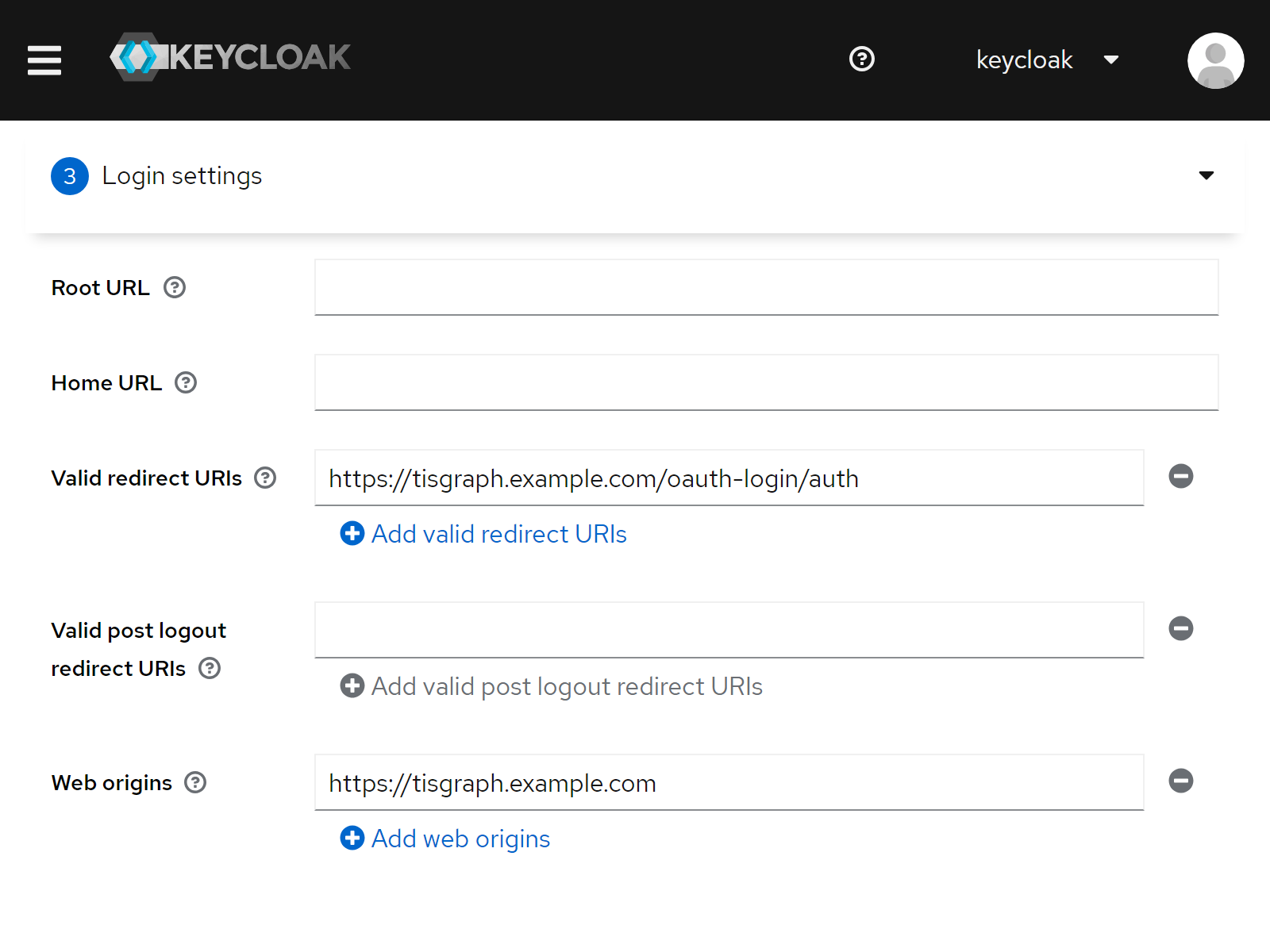
| 7 | Root URL | <empty> |
| 8 | Home URL | <empty> |
| 9 | Valid redirect URIs | https://tisgraph.example.com/oauth-login/auth |
| 10 | Web origins | https://tisgraph.example.com |
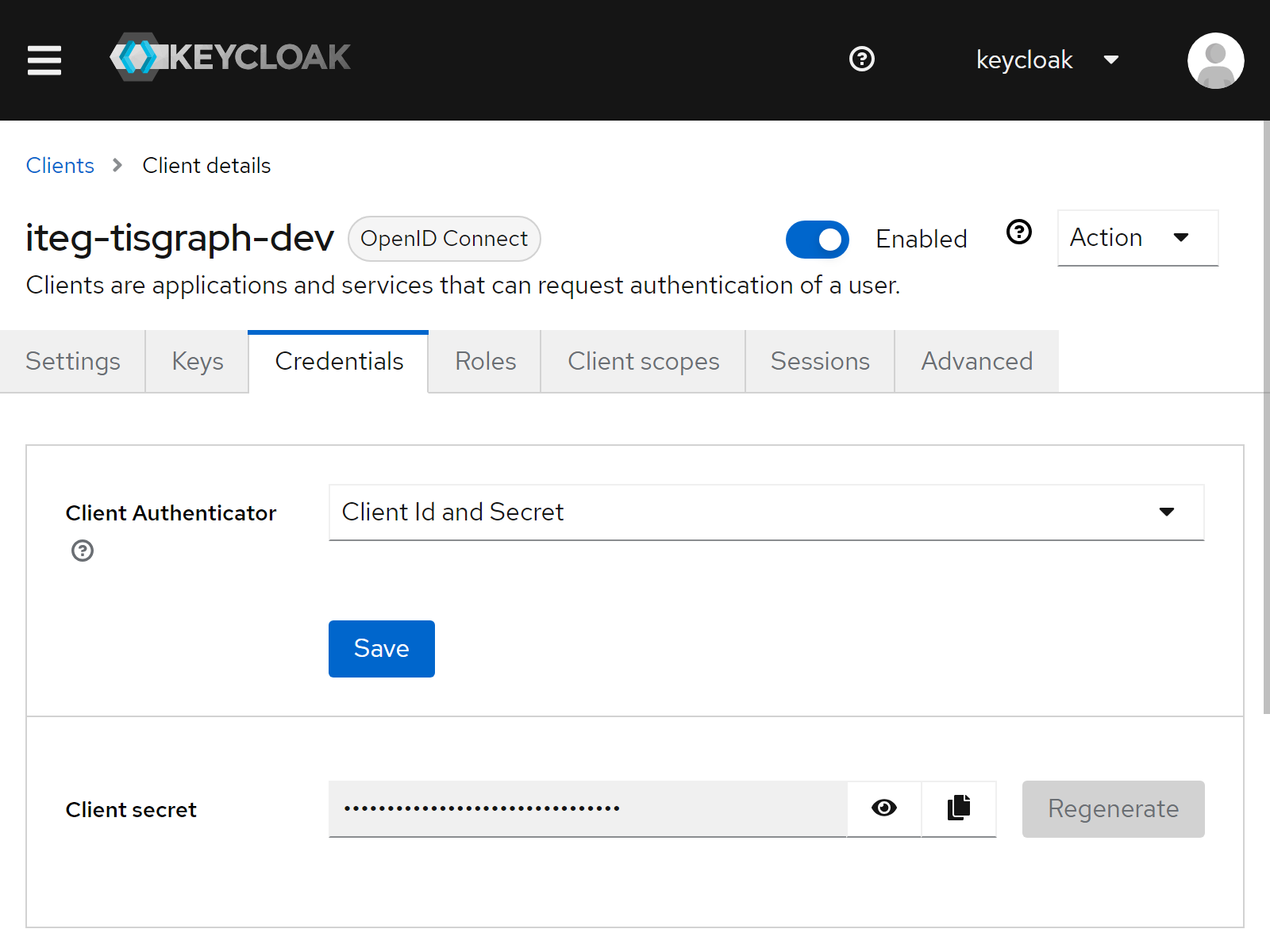
Navigate to the newly created client, open the tab "Credentials", and copy the "Client secret" to the clipboard.
Configure TISGraph
Configure org.clazzes.login.oauth. In at.iteg.tis.graph, configure users.suPrincipal and delegateLoginMechanism and apiSecurityContext. Open https://tisgraph.example.com/oauth-login/login in order to try or debug the OAuth authentication.
Migrate Users in Existing Installations
If you have an existing TISGraph installation, you might consider to change the existing users in the database from WISKI authentication to OAuth in order to avoid the need to manually re-assing group membership of these user.
After having configured access to the OSGI console you can change existing users to the new OAuth login using the following commands:
iteg@gogo> query -l 60 TISGRAPH "select ID,USER_STRING from tisgraph_user where USER_STRING like 'at.iteg.wdb.api.dto.WiskiPrincipal::%'"
iteg@gogo> query TISGRAPH "update tisgraph_user set USER_STRING=REPLACE(USER_STRING,'at.iteg.wdb.api.dto.WiskiPrincipal::','org.clazzes.login.oauth.OAuthPrincipal::') where USER_STRING like 'at.iteg.wdb.api.dto.WiskiPrincipal::%'"Configure IIS
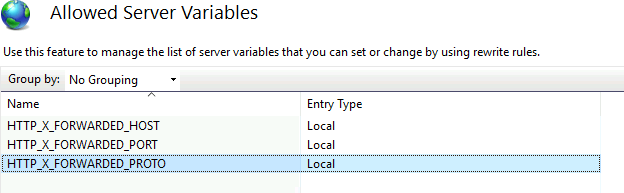
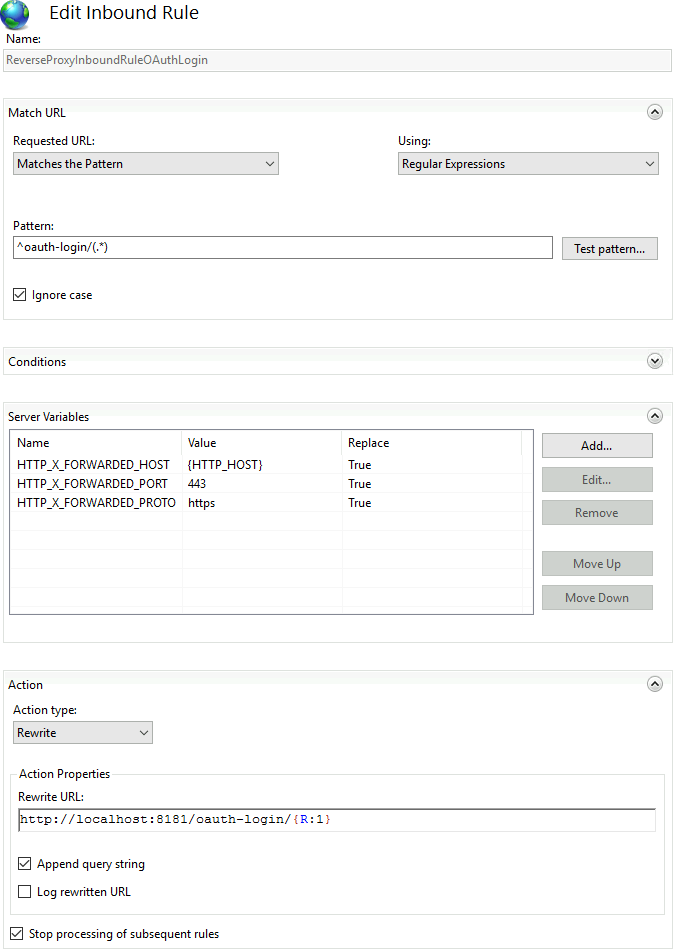
If the IIS (Internet Information Services for Windows Server) is used as reverse proxy, make sure that /oauth-login is proxied to TISGraph running on localhost:8181. Furthermore, make sure that the HTTP headers HTTP_X_FORWARDED_HOST, HTTP_X_FORWARDED_PORT, HTTP_X_FORWARDED_PROTO are set correctly. This is necessary as TISGraph needs to construct a redirect_uri for the authentication flow.
<rule name="ReverseProxyInboundRuleOAuthLogin" stopProcessing="true">
<match url="^oauth-login/(.*)" />
<action type="Rewrite" url="http://localhost:8181/oauth-login/{R:1}" />
<serverVariables>
<set name="HTTP_X_FORWARDED_HOST" value="{HTTP_HOST}" />
<set name="HTTP_X_FORWARDED_PORT" value="443" />
<set name="HTTP_X_FORWARDED_PROTO" value="https" />
</serverVariables>
</rule>